
PDF + Testing Engine
Testing Engine (only)
PDF (only)

Western Governors University's (WGU) Secure Software Design exam is a crucial evaluation for students interested in a career in software development with a cybersecurity concentration. Examinees must demonstrate their ability to apply fundamental concepts of threat modeling, software architecture, and safe coding to real-world situations to create resilient software to the constantly changing world of cyberattacks.
This C706 exam is a crucial stage in your development as a capable and accountable software developer, whether your goal is to demonstrate your proficiency in building reliable, secure systems or to solidify your understanding of security best practices.
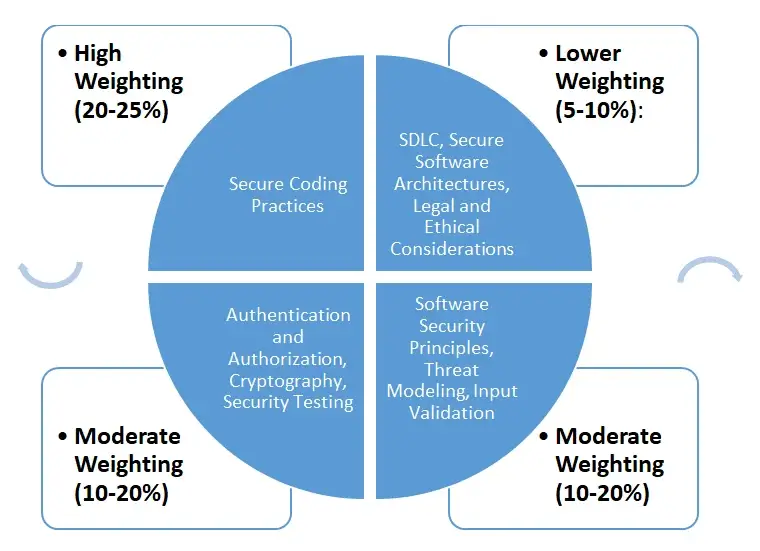
| Topic | Description |
|---|---|
| Software Security Principles (15-20%) | Core principles such as least privilege, defense in depth, and separation of duties are foundational and often receive significant emphasis. |
| Threat Modeling (10-15%) | Identifying and analyzing potential threats is crucial for secure design, so expect a moderate focus on this area. |
| Secure Coding Practices (20-25%) | Since writing secure code is a practical skill, this area is likely to be heavily weighted, covering various vulnerabilities and how to prevent them. |
| Input Validation (10-15%) | Input validation is a critical aspect of secure coding, so it might be combined with secure coding practices or treated as a distinct, important topic. |
| Authentication and Authorization (10-15%) | Ensuring secure user access is essential, so this topic will likely be moderately weighted. |
| Cryptography (10-15%) | Understanding encryption and secure data handling is important, but the focus is often on practical application rather than deep mathematical theory. |
| Security Testing (10-15%) | Testing for vulnerabilities is crucial, so expect questions on tools and methodologies used to test software security. |
| Software Development Lifecycle (SDLC) (5-10%) | While integrating security into the SDLC is important, it might have less weight compared to more technical topics. |
| Secure Software Architectures (5-10%) | Designing secure architectures is a higher-level skill, so it might receive moderate weighting, depending on its integration with other topics. |
| Legal and Ethical Considerations (5-10%) | This area is typically less weighted but still important, especially in understanding compliance and ethical issues related to software security. |
Trust the simple Secure-Software-Design Questions Answers from DumpsGenious to help you succeed the first time around with a 100% money-back guarantee! The fantastic Secure-Software-Design real exam questions and answers have helped thousands of IT professionals get their desired certification.
The exam questions and answers are straightforward and beneficial for all candidates, no complexity is involved. The questions and answers on DumpsGenious are jam-packed with the most recent and pertinent material available because the specialists there put in their best effort to create them. So keep calm, cox’ you are in safe hands
DumpsGenious Secure-Software-Design dumps are equally fantastic. They exclusively concentrate on the most crucial areas of your exam and provide you with the best knowledge available in an approachable, interactive language.
Consider advancing your career by using this trusted strategy for passing exams. The Secure-Software-Design braindumps are exceptional and a treat for those who want to excel in their career but, despite time restrictions, wish to attempt the Secure-Software-Design exam. Most of these exam dumps questions will likely be present in your genuine Secure-Software-Design exam.
What are the three primary goals of the secure software development process?
A. Performance, reliability, and maintainability
B. Cost, speed to market, and profitability
C. Redundancy, scalability, and portability
D. Confidentiality, integrity, and availability
In which step of the PASTA threat modeling methodology will the team captureinfrastructure, application, and software dependencies?
A. Attack modeling
B. Define technical scope
C. Define objectives
D. Risk and impact analysis
The software security team prepared a detailed schedule napping security developmentlifecycle phases to the type of analysis they will execute.Which design and development deliverable aid the team prepare?
A. Design security review
B. Updated threat modeling artifacts
C. Privacy implementation assessment results
D. Security test plans
An individual is developing a software application that has a back-end database and isconcerned that a malicious user may run the following SOL query to pull information aboutall accounts from the database:Which technique should be used to detect this vulnerability without running the source codes?
A. Dynamic analysis
B. Cross-site scripting
C. Static analysis
D. Fuzz testing
The software security team is performing security testing for a new software product that isclose to production release. They are concentrating on integrations between the newproduct and database servers, web servers, and web services.Which security testing technique is being used?
A. Fuzz testing
B. Dynamic code analysis
C. Binary fault injection
D. Binary code analysis
Which type of threat exists when an attacker can intercept and manipulate form data afterthe user clicks the save button but before the request is posted to the API?
A. Elevation of privilege
B. Spoofing
C. Tampering
D. Information disclosure
Features have been developed and fully tested, the production environment has beencreated, and leadership has approved the release of the new product. Technicians havescheduled a time and date to make the product available to customers.Which phase of the software development lifecycle (SDLC) is being described?
A. Maintenance
B. Deployment
C. End of life
D. Testing
Using a web-based common vulnerability scoring system (CVSS) calculator, a securityresponse team member performed an assessment on a reported vulnerability in the userauthentication component of the company's now product. The base score of thevulnerability was 8.3 and changed to 9.4 after adjusting temporal and environmentalmetrics.Which rating would CVSS assign this vulnerability?
A. High seventy
B. Critical severity
C. Medium severity
D. Low seventy
Company leadership has discovered an untapped revenue stream within its customer baseand wants to meet with IT to share its vision for the future and determine whether to moveforward.Which phase of the software development lifecycle (SDLC) is being described?
A. Implementation
B. Design
C. Planning
D. Requirements
The security team is reviewing whether changes or open issues exist that would affectrequirements for handling personal information documented in earlier phases of thedevelopment life cycle.Which activity of the Ship SDL phase is being performed?
A. Vulnerability scan
B. Final security review
C. Open-source licensing review
D. Final privacy review

TESTED 28 October 2023
 Noah Jones
Nov 21, 2024
Noah Jones
Nov 21, 2024
The most updated and efficient knowledgeable Secure-Software-Design questions & answers are available on the Dumpsgenious that will help you to pass WGU Secure Software Design (KEO1) Exam easily. Other than that, their different features will surprise you all. Anthony Mckinney
Nov 20, 2024
Anthony Mckinney
Nov 20, 2024
I was recommended to prepare Secure-Software-Design Questions & Answers from the Dumpsgenious, and it was worth recommending. The result was beyond my expectations that help to excel in my professional career. Simon Myers
Nov 20, 2024
Simon Myers
Nov 20, 2024
If you are thinking of preparing for WGU Secure Software Design (KEO1) Exam, then I will recommend Dumpsgenious. This platform is providing such services for many years with remarkable results for the students.